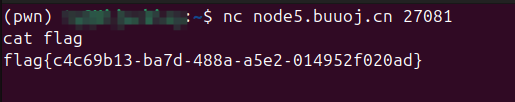
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
| int sub_80486BB()
{
alarm(0x3Cu);
signal(14, handler);
setvbuf(stdin, 0, 2, 0);
setvbuf(stdout, 0, 2, 0);
return setvbuf(stderr, 0, 2, 0);
}
int __cdecl sub_804871F(int buf)
{
size_t n; // eax
char s[32]; // [esp+Ch] [ebp-4Ch] BYREF
char bufa[32]; // [esp+2Ch] [ebp-2Ch] BYREF
ssize_t v5; // [esp+4Ch] [ebp-Ch]
memset(s, 0, sizeof(s));
memset(bufa, 0, sizeof(bufa));
sprintf(s, "%ld", buf);
v5 = read(0, bufa, 0x20u);
bufa[v5 - 1] = 0;
n = strlen(bufa);
if ( strncmp(bufa, s, n) )
exit(0);
write(1, "Correct\n", 8u);
return (unsigned __int8)bufa[7];
}
ssize_t __cdecl sub_80487D0(char nbytes)
{
_BYTE buf[231]; // [esp+11h] [ebp-E7h] BYREF
if ( nbytes == 127 )
return read(0, buf, 0xC8u);
else
return read(0, buf, nbytes);
}
int main()
{
int buf; // [esp+4h] [ebp-14h] BYREF
char v2; // [esp+Bh] [ebp-Dh]
int fd; // [esp+Ch] [ebp-Ch]
sub_80486BB();
fd = open("/dev/urandom", 0);
if ( fd > 0 )
read(fd, &buf, 4u);
v2 = sub_804871F(buf);
sub_80487D0(v2);
return 0;
}
|